
Current Research Topics
- Proactive, Adaptive Moving Target Defense
- Defensive Cyberdeception
- Decision Making with Uncertain Opinions
- Cyber Resilience & Influence
- Metrics & Measurements
- Trust-based Security & Privacy Applications
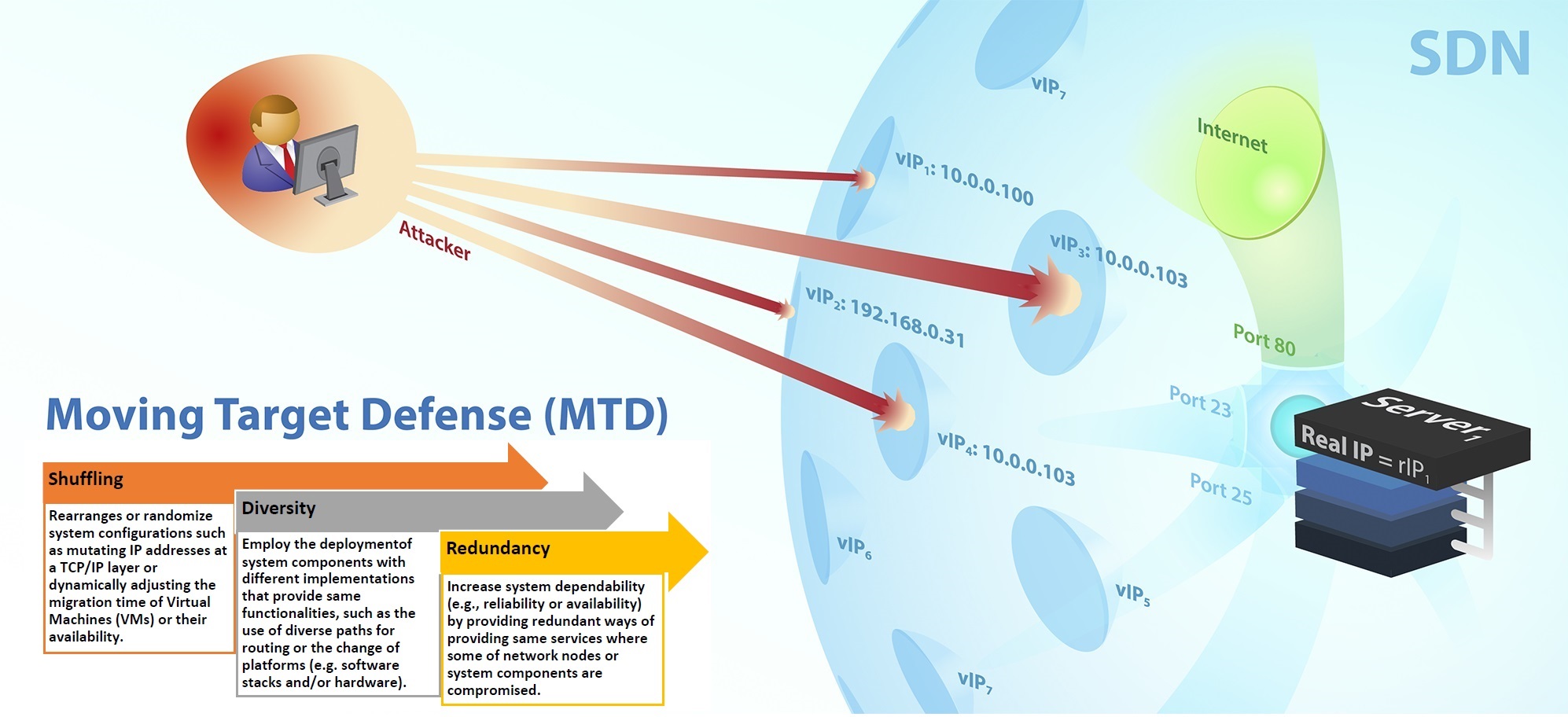
Proactive, Adaptive Moving Target Defense
Moving Target Defense (MTD) is to increase confusion and uncertainty for attackers by dynamically changing attack surface. Various types of MTD techniques have been developed in the state-of-the-art approaches by using techniques including shuffling, diversity, and/or redundancy. In this research, we aim to develop adaptive, scalable, and affordable MTD techniques that can meet the required levels of system performance and security while offering affordable defense cost allowed by the resource-constrained system envronments.
Key collaborators: University of Canterbury (Prof. Dong Seong Kim's group), New Zealand, Gwangju Institute of Science and Technology (GIST: Prof. Hyuk Lim's group), Republic of Korea, and US Army Research Laboratory (Dr. Terrence J. Moore, Dr. Frederica F. Nelson, and Dr. Noam Ben-Asher).
Selected Related Technical Papers:
- J.H. Cho and N. Ben-Asher, “Cyber Defense in Breadth: Modeling and Analysis of an Integrated Defense Mechanism,” The Journal of Defense Modeling and Simulation, vol. 15, no. 2, April 2018.
- D. P. Sharma, D. S. Kim, S. Yoon, H. Lim, J.H. Cho, and T. Moore, “FRVM: Flexible Random Virtual IP Multiplexing in Software-Defined Networking,” The 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (IEEE TrustCom 2018), Aug. 2018.
- J.H. Cho and T. J. Moore, “Software Diversity for Cyber Resilience: Percolation Theoretic Approach,” Nature-Inspired Cyber Security and Resilience: Fundamentals, Technology and Applications, 2018, Editors (E. M. El-Alfy, et al.), IET (under press)
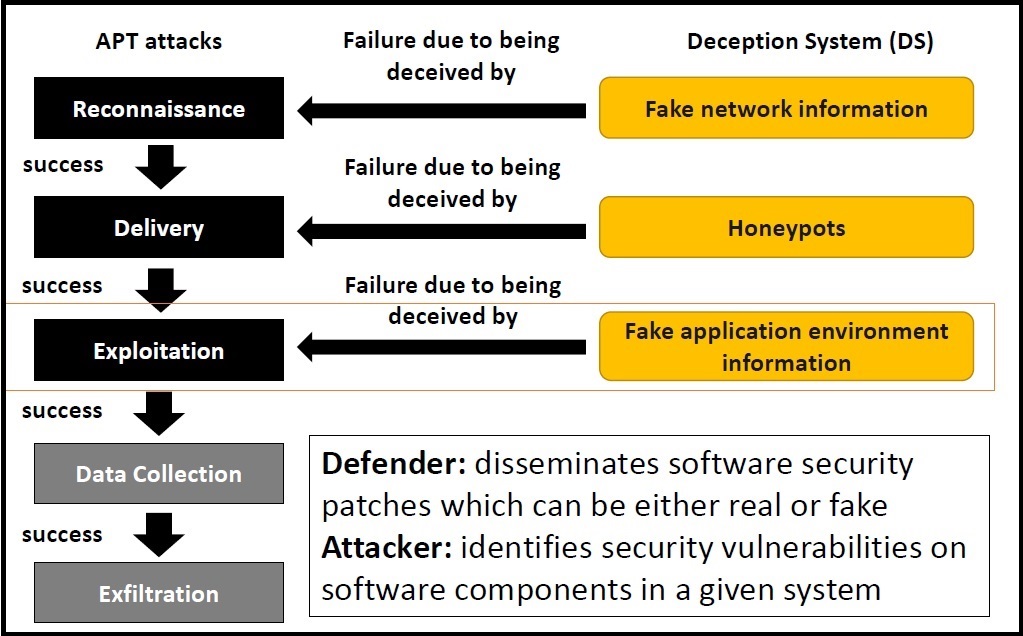
Defensive Cyberdeception
Defensive cyberdeception has been used to thwart or confuse attackers by actively deceiving the attackers (e.g., honeypots or honeynets) and/or disseminate fake information which can substantially hinder the attacker's strategies to collect useful information towards the given system. We take game theoretic approaches, particularly hypergame theory and/or Interactive Partially Observable Markov Decision Process (I-POMDP), in order to model the interactions between attackers and defenders.
Key collaborators: North Carolina State Univerisity, NC (Prof. Munindar's group) and US Army Research Laboratory (Dr. Charles Kamhoua).
Selected Related Technical Papers:
- J.H. Cho, M. Zhu, and M. Singh, “Modeling and Analysis of Deception Games based on Hypergame Theory,” an invited book chapter in the book entitled `Automated Cyber Deception', Springer, June 2018 (under press).
- M. Ge, J.H. Cho, C. Kamhoua, and D. S. Kim, “Optimal Deployments of Defense Mechanisms for Internet of Things,” The International Workshop on Secure Internet of Things 2018 (SIoT 2018), in conjunction with the European Symposium on Research in Computer Security (ESORICS 2018), Sept. 2018.

Decision Making with Uncertain Opinions
This research investigates how uncertain opinion can affect decision performance. We first investigated how the concept of uncertainty can be defined. In particular, we looked at how a subjective opinion can be formulated based on different causes of uncertainty. We used the formulation of Subjective Logic (SL) to enhance its current form. Another direction is to maximize decision performance based on machine learning algorithms in inferring unknown opinions in the presence of corrupted information. Another direction of this research is to maximize the accuracy of decision making where some opinions are missing or conflicting to other neighboring opinions by using machine learning (or deep learning) algorithms such as graph convolutional neural networks (GCNN) or gated recurrent units (GRU) as a variant of recurrent neural networks (RNN). We examined the performance of our proposed DL-based algorithms using a large-scale network datasets.
Key collaborators: University of Oslo, Norway (Prof. Audun Josang's group), SUNY-Albany, NY (Prof. Feng Chen's group), RPI, NY (Prof. Sibel Adali's group)
Selected Related Technical Papers:
- X. Zhao, F. Chen, and J.H. Cho, “A Deep-Learning based Scalable Inference of Uncertain Opinions,” The IEEE International Conference on Data Mining (ICDM 2018), Nov. 2018.
- A. Josang, J.H. Cho, and F. Chen, “Uncertainty Characteristics of Subjective Opinions,” 21st International Conference on Information Fusion (FUSION 2018), July 2018.
- J.H. Cho and S. Adali, “Is Uncertainty Always Bad?: Effect of Topic Competence on Uncertain Opinions,” IEEE International Conference on Communications (ICC 2018), May 2018. (Highlighted at the EurekAlert!)
- F. Chen, C. Wang, and J.H. Cho, “Collective Subjective Logic: Scalable Uncertainty-based Opinion Inference,” 2017 IEEE International Conference on Big Data (BigData 2017), Dec. 2017.
- J.H. Cho, T. Cook, S. Rager, J. O’Donovan, and S. Adali, “Modeling and Analysis of Uncertainty-based False Information Propagation in Social Networks,” IEEE Global Communications Conference (GLOBECOM 2017), Dec. 2017. (Best Paper Award; Highlighted at the EurekAlert!)
- J.H. Cho, “Dynamics of Uncertain and Conflicting Opinions in Social Networks,” IEEE Transactions on Computational Social Systems, vo. 5, no. 2, pp. 518-531, June 2018.
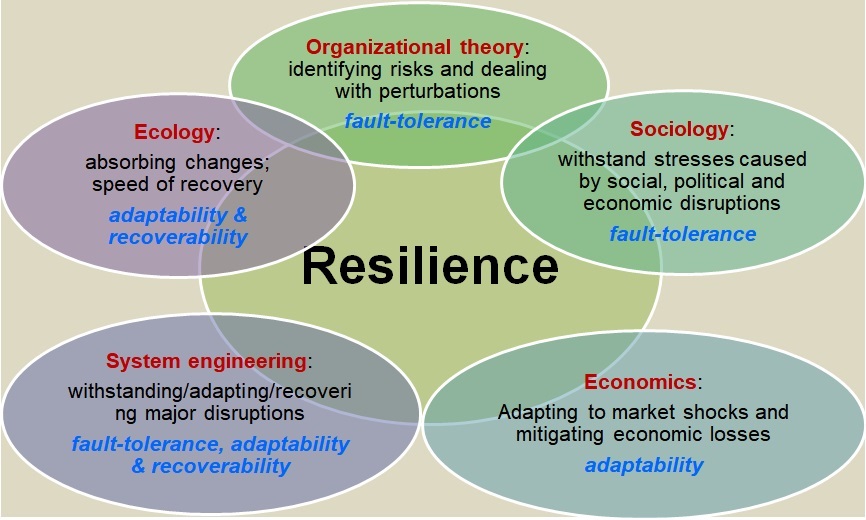
Cyber Resilience & Influence
This research aims to develop cyber systems that are highly resilient against attacks, agile for sudden, unexpected failures, and trustworthy in providing normal services even in the presence of hostile entities in networks. Our recent work took percolation-based network adaptations or software diversity based network adaptations for maximizing network connectivity but minimizing security vulnerability in networks for mission-oriented applications. Further, a variety of influence (or centrality) metrics are revisited in this research to refine them further to be applied in the context of mission-oriented systems or applications, which need to consider the characteristics of contested network environments such as resource constraints/utilization, mission success with hierarchical multi-task mission teams, and/or service availability based on network connectivity.
Key collaborators: US Army Research Laboratory (Dr. Terrence J. Moore).
Selected Related Technical Papers:
- J.H. Cho and T. Moore, “Percolation-based Network Adaptability under Cascading Failures,” IEEE INFOCOM 2018, April 2018. (Best-in-Session Presentation Award)
- J.H. Cho and T. J. Moore, “Software Diversity for Cyber Resilience: Percolation Theoretic Approach,” Nature-Inspired Cyber Security and Resilience: Fundamentals, Technology and Applications, 2018, Editors (E. M. El-Alfy, et al.), IET (under press)
- T. Moore and J.H. Cho, “Chapter 6: Applying Percolation Theory,” an invited book chapter to the book entitled Cyber Resilience: Cyber Resilience of Systems and Networks (Editors: A. Kott and I. Linkov), pp. 107-133, June 2018, Springer Nature.
- J.H. Cho and J. Gao, “Cyber War Game in Temporal Networks,” vol. 11, no. 2, PLoS One, Feb. 2016
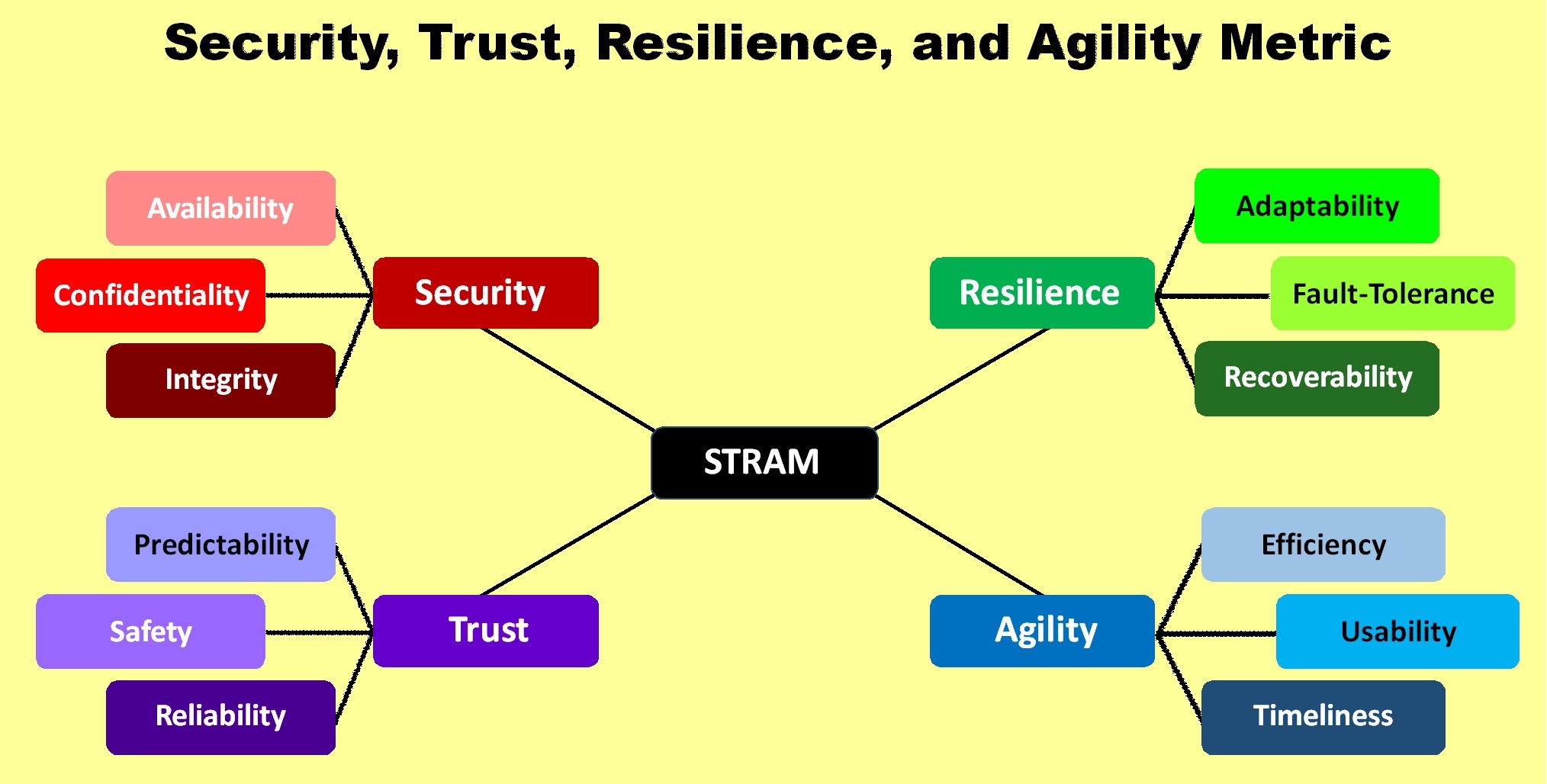
Metrics & Measurements
This research aims to develop system-level metrics to measure security, trust, resilience, and agility of a cyber-physical system. As modern cyber-physical systems become more complicated ever in which the system is required to deal with various types of problems associated with hardware, software, networks, human factors, and physical environments, measuring useful and meaningful metrics efficiently is not a trivial task. In this research, we have developed a suite of system-level metrics that capture dynamic aspects of a given system in terms of resilience and agility. We have developed the so called `STRAM' which stands for `security, trust, resilience, and agility metric' framework, in order to estimate the multidimensional quality of a given system in terms of both static and dynamic quality of measures and metrics.
Key collaborators: University of Texas at San Antonio, TX (Prof. Shouhuai Xu's group)
Selected Related Technical Papers:
- J.H. Cho, S. Xu, P. Hurley, M. Mackay, T. Benjamin, and M. Beaumont, “STRAM: Measuring the Trustworthiness of Computer-based Systems,” accepted to ACM Computing Surveys, Sept. 2018.
- P. Du, Z. Sun, H. Chen, J.H. Cho, and S. Xu, “Statistical Estimation of Malware Detection Metrics in the Absence of Ground Truth,” IEEE Transactions on Information Forensics and Security, vol. 13, no. 12, pp. 2965-2980, Dec. 2018.
- M. Pendleton, R. Garcia-Lebron, J.H. Cho, and S. Xu, “A Survey on Systems Security Metrics,” ACM Computing Surveys, vol. 49, no. 4, Article No. 62, Jan. 2017.
- H. Chen, J.H. Cho, and S. Xu, “Quantifying the Security Effectiveness of Firewalls and DMZs,” Hot Topics in the Science of Security (HotSoS’2018), April 2018.
- J.H. Cho, S. Xu, P. Hurley, M. Mackay, T. Benjamin, and M. Beaumont, “STRAM: Measuring the Trustworthiness of Computer-based Systems,” revised/submitted to ACM Computing Surveys, March 2018
- J.H. Cho, P. Hurley, and S. Xu, “Metrics and Measurement of Trustworthy Systems,” IEEE Military Communications Conference (MILCOM 2016), Nov. 2016.
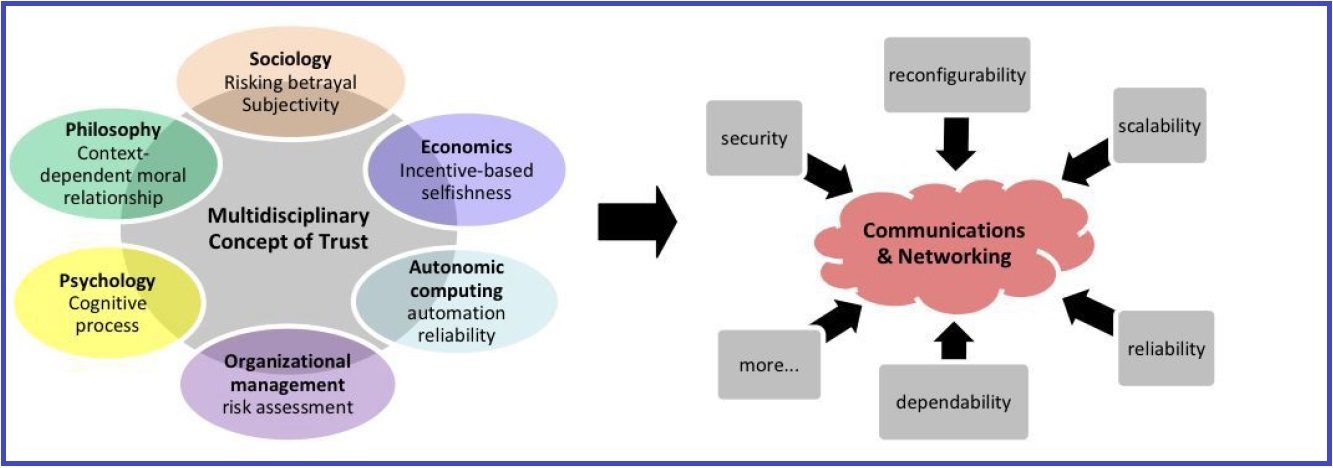
Trust-based Security & Privacy Applications
This research adopts the multidisciplinary concept of trust to develop trust models for communication networks as well as social networks. Trust metrics / models are developed to consider unique characteristics of a given network and used to develop a variety of network security applications, including secure routing, access control, key management, and intrusion detection. Further, many trust-based approaches are developed for applications for mission-oriented tactical environments. Our recent effort is going towards estimating human trust and the relationships between trust, privacy, and social capital in online social networks.
Key collaborators:
US Army Research Laboratory (Dr. Ananthram Swami, Dr. Kevin Chan, Dr. Hasan Cam), Virginia Tech, VA (Prof. Ing-Ray Chen's group), RPI, NY (Prof. Sibel Adali's group), KAIST, ROK (Prof. Dongman Lee's group).
Selected Related Technical Papers:
- J.H. Cho and I.R. Chen, “PROVEST: Provenance-based Trust Model for Delay Tolerant Networks,” IEEE Transactions on Dependable and Secure Computing, vol. 15, no. 1, Jan./Feb. 2018.
- B. Gwak, J.H. Cho, D. Lee, and H. Son, “TARAS: Trust-Aware Role-based Access Control System in the Public Internet-of-Things,” The 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (IEEE TrustCom 2018), Aug. 2018.
- Y. Wang, I.R. Chen, J.H. Cho, and J. Tsai, “Trust-Based Task Assignment with Multi-Objective Optimization in Service-Oriented Ad Hoc Networks,” IEEE Transactions on Network and Service Management, vol. 14, no. 1, pp. 217-232, Mar. 2017.
- J.H. Cho, I. Alsmadi, and D. Xu, “Privacy and Social Capital in Online Social Networks,” IEEE Global Communications Conference (GLOBECOM 2016), Dec. 2016.
- J.H. Cho, H. Cam, and A. Oltramari, “Effect of Personality Traits on Trust and Risk to Phishing Vulnerability: Modeling and Analysis,” IEEE International Multi-Disciplinary Conference on Cognitive Methods in Situation Awareness and Decision Support (CogSIMA 2016)
- Y. Wang, I.R. Chen, J.H. Cho, A. Swami, Y.C. Lu, C.T. Lu, and J. Tsai “CATrust: Context-Aware Trust Management for Service-Oriented Ad Hoc Networks,” IEEE Transactions on Service Computing, June 2016, early access version available.
- J.H. Cho, I.R. Chen, and K. Chan, “Trust Threshold based Public Key Management in Mobile Ad Hoc Networks,” Ad Hoc Networks, vol. 44, pp. 58-75, July 2016.
- J.H. Cho, K. Chan, and S. Adali, “A Survey on Trust Modeling,” ACM Computing Surveys (CSUR), vol. 48, no.2, Article No. 28, Oct. 2015.
- S. Adali, K. Chan, and J.H. Cho, “TANDEM: A Trust-based Agent Framework for Networked Decision Making,” Computational and Mathematical Organization Theory (CMOT), vol. 21, no. 4, Springer, Dec. 2015, pp. 461-490.
- J.H. Cho, “Tradeoffs between Trust and Survivability for Mission Effectiveness in Tactical Networks,” IEEE Transactions on Cybernetics, vol. 45, no. 5, pp. 754-766, April 2015.